Image: succo/Pixabay
Information security is old news. From the schadenfreude-inducing (the infamous Sony hack) to the unsettling (76 million records stolen from financial services company JP Morgan Chase), we’ve seen almost every kind of breach — and resulting consequences — imaginable.
The focus has been on enabling secure business interactions. Behavior such as selling items on your smartphone and getting payment notifications within minutes are becoming more common. With an increased business produced customer-facing apps, there are risks associated when extending access out to devices for sensitive information. This is where mobile identity plays a critical role, presenting the opportunity to improve the security of accessing sensitive corporate information.
The consequences can be quite serious for businesses that are still vulnerable. The average service disruption [PDF] costs $53,000 USD per minute and averages $1 million USD due to downtime, idle time, technical support, and forensics.
The key is in the identity
You’re likely already familiar with basic information security practices, and the concepts of securing data in motion and data at rest.
But what if your company isn’t dealing in financial secrets or healthcare records (or cheating spouses)? What if your mobile messaging consists of casual, non-vital chatter that would be no threat to anyone or anything if released?
Do you still need to be worried about security? Businesses in industries without strict regulations on corporate communications, who simply don’t need the highest levels of security, should be thinking about identity rather than security.
Think about it this way:
There’s little danger of consequences from a security breach in cases where your messages aren’t particularly sensitive, but there’s still a real cost if they get out of hand.
For instance, say you have employees who clock in and out of shifts via SMS messages. Is that a matter of national security? Of course not.
You do, however, need to verify that it’s the employee who’s checking in — rather than a friend — to ensure that your payroll is correct and employees aren’t reporting incorrect hours. This is a form of “spoofing,” a situation in which one person (or program) online pretends to be someone else.
Spoofing can happen via SMS, email, or even websites that require usernames and passwords. After all, it’s easy enough to send a username and password combination to a friend or family member, and anyone who’s able to use moderately sophisticated technology can spoof an SMS or email account.
“SMS spoofing works around the world on almost every mobile network as far as we know.” -SMSspoofing.com
This is where identity comes in. You need to be able to authoritatively identify the sender of the message, in this case. (In other areas, such as sensitive corporate broadcasts, it could be the recipient of a message who needs to be verified.)
Using identity verification to stop spoofing
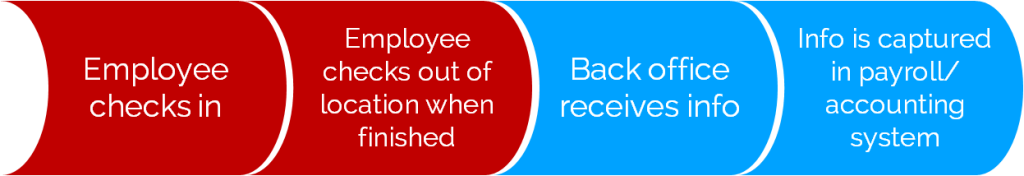
Verifying exactly who is sending and receiving messages on behalf of the business becomes even more important in workflow messaging. Let’s look at the timesheet example again.
If the mobile messaging tool you’re using (an app or SMS) can be easily fooled, employees could be fudging hours by having a friend check in and out.
The red steps in the workflow below indicate the points at which information could be easily spoofed when using mobile and/or SMS messages to report employee work hours.
Luckily, this particular problem is relatively easy to solve. Look for mobile messaging solutions that:
- Avoid SMS, or use it only as a backup
- Require the user to enter a PIN to access the app
- Use public and private keys to ensure the app can’t be altered or replicated on other devices
- In the event of a lost or stolen mobile device, use a new installation of the app to both replace and disable the old app
A solution that already meets these specifications will protect you against this kind of spoofing out of the box, with no security work needed. You’ll know who is sending and receiving messages on your behalf every single time.
Take a look at how one business used our award-winning mobile messaging app GAMMA to prevent timesheet spoofing, or learn more about GAMMA by clicking on the button below.