How to enable 2FA in my business?
The complete guide about two-factor authentication
Table of contents
Cybercriminals are expanding complex techniques to evade security systems and steal valuable business data. This is the reason why most companies want to implement two-factor authentication to improve their online accounts’ security. If you want to learn how to enable 2FA, you are in the right place.
Cyberattacks were one of the top five risks businesses faced in 2020. The pandemic left many companies with a hybrid office/remote work model, which means more devices accessing networks, systems and applications from many more locations. Training your employees, customers and users on the importance of secure passwords is no longer enough. Neither is only protecting online accounts with single-factor authentication.
According to a NordPass’ report, the top three most-used passwords in 2020 were 123456, 123456789, and picture1. Next on the list were just password2, qwerty, and abc123. Password vulnerabilities are just one of the causes of cyberattacks. Hacking and credential theft are more common than ever, along with the holes your systems are likely to have.
Your information is at risk, and at any time, you could be the victim of a cyberattack and suffer the financial and reputational damages it entails – from lost revenue, angry and lost customers and bad public relations to potential legal costs. As mobile security experts, we recommend that businesses act before the attack occurs. Then it will be too late.
Which types of authentication exist?
- Single-factor authentication: It’s when users only need their username and primary password to access an account.
- Two-factor authentication: It’s a security method that helps confirm users’ identity by asking for a second factor of authentication after submitting their username and password – commonly a code or one-time password sent by SMS to their mobile devices.
- Multi-factor authentication: It’s a security method that asks users for two or more details – contextual, time-based factors or biometrics – before giving access to their accounts.
In this guide, we will explain everything about how to enable two-factor authentication in your business and how it makes your user authentication process more secure.
What is two-factor authentication
Two-factor authentication, or 2FA, is an effective security method to confirm the identity of the users with two different pieces of information before giving access to accounts, data, and resources.
- After entering their username and password, the users will need to provide a second password or code sent to a separate location – commonly via SMS or IP to the personal mobile device.
- The second password, also known as one-time password, is a unique, time-sensitive security token that expires in a pre-defined time (e.g., 5 minutes).
With 2FA enabled, knowing the password of a bank account or work email isn’t enough to have full access. They would need the primary password and the temporary one sent to another device.
This security method is so effective that businesses and organizations worldwide use it internally to monitor and protect their information and networks. Also, they are encouraging their final users to add it to protect their accounts and data.
There are different 2FA categories:
- Information you only know: It can be the answer to a personal question, a second password, or a one-time code sent to a personal device.
- Information you only have: It can be a credit card number, a hardware token, or a detail of your ID.
- Biometric: Like a fingertip, voice print or iris scan. This option is the newest, becoming popular with the latest smartphones.
Is 2-factor authentication secure?
2FA is an extra layer of security that makes life more difficult for hackers.
In 2021, Google announced that it would make 2FA mandatory for over 150 million users because of being one of the “most reliable ways to prevent unauthorized access to accounts and networks”.
According to Google research, SMS code sent to a recovery phone number helped block 100% of automated bots, 96% of bulk phishing attacks, and 76% of targeted attacks.
Two-factor authentication is not only secure, but it’s also convenient. Your users will appreciate your protecting them with almost no effort from their side.
By receiving an OTP SMS, users only must copy the code, or in some cases, the code is copied automatically without typing it.
Of course, OTP should be considered as an extra layer of security, and must be combined with other security solutions like a WAF, CASB, etc.
Two-factor authentication is an excellent security method to enhance your employees’ and users’ security and reduce the probability of security breaches.
MFA vs Two-factor authentication. Are they the same?
Quick response: two-factor and multi-factor authentication are similar but not identical. 2FA asks users for a second authentication factor to access their accounts – SMS message, one-time passwords or push notifications – while MFA goes beyond 2FA and asks for two or more validation methods, such as facial recognition, location-based factors, or fingerprint scan.
Both authentication methods have the same objective: to confirm the user’s identity before giving access to personal and valuable information.
The main difference is that 2FA asks for two different types of passwords, while multi-factor authentication adds other two or more methods.
MFA could be more secure than 2FA because hackers need more information to succeed. But businesses and organizations should consider the friction a multi-factor authentication can cause their users.
We have mentioned that one of the great benefits of 2FA via SMS is that it’s not only secure but also accessible and easy to use. Customers and employees want to feel safe and wish for seamless experiences.
How does 2FA work?
There are different types of 2FA, and each of them works differently. Let’s see them in detail:
SMS 2FA
Users must provide their mobile phone numbers to enable the 2FA method. Every time they want to log in to their accounts, they must enter a code received via SMS after completing their usernames and passwords.
2FA via SMS is one of the most used authentication methods because it is easy to implement – no need to download an additional app – and it is universal – almost everyone has an SMS-capable phone number.
2FA Authenticator App
With the 2FA Authenticator App, users will also need a second code after logging in with their usernames and passwords. But in this case, they have to use an application to receive the new code.
One of the most famous authenticator apps is Google Authenticator. This type of 2FA has its cons and pros. The main difference with the SMS style is that, in this case, users don’t need to be connected to a mobile network to receive the code because it is stored physically on their phones.
An authenticator App is also effective for protecting websites. Websites with 2FA will show users a QR code. Once users scan it, the authenticator app will create new passwords every 30 seconds.
Push-based 2FA
Users will receive a prompt to their devices during the login with the possible location where they are trying to access. Users can approve or deny the attempt, whether they are the ones trying to gain access.
Why is 2FA required?
Some businesses are requiring 2FA through policy because of its great benefits.
- It reduces the probability of a security breach.
- It lowers the total costs of disruption.
- It lowers the reputation risk following a security breach.
- It’s an additional layer of protection against identity theft and password phishing.
- It’s an extra layer of protection against keystroke loggers.
- It further thwarting of packet sniffing attempts.
Plus, adding MFA raises security scores. You can train your employees on the benefits and usage of 2FA and invest in a solution that brings its benefits to all access points in the business, not just the password vault.
But there are many other important reasons why most businesses require 2FA for their employees and final users. One of them is the enormous negative impact of cyber-attacks and security breaches.
Why do we need to implement 2FA?
Still not convinced? Let’s see some surprising numbers:
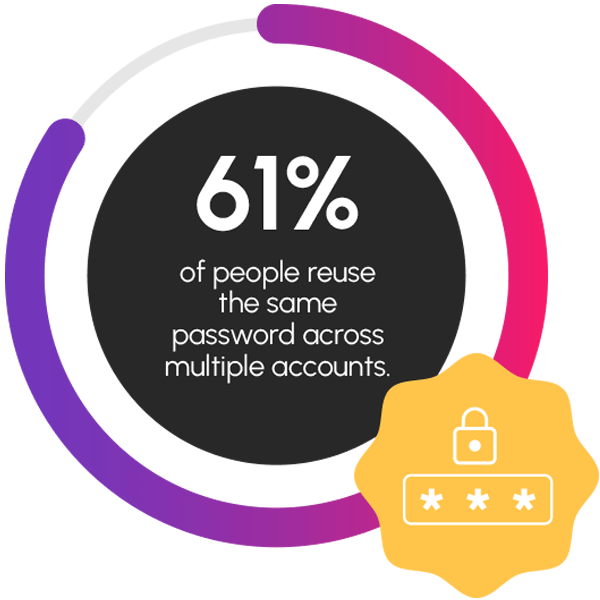
- 61% of people reuse the same password across multiple accounts: People not only use weak passwords, but they also tend to repeat them for different accounts. Suppose your employees use a strong password but repeat it for their social media, bank account and email. If hackers guess one, they can have access to all the others.
- eCommerce retailers face 206,000 cyberattacks each month: According to Signal Sciences, the eCommerce industry is the one that is suffering more data breaches and cyberattacks. The average recovery cost from eCommerce fraud reached $6.4 billion in 2021.
- The American government spent $18.8 billion on recovery costs in 2020: American City and County reported the average impact of downtime and recovery following a cyberattack. Companies risk losing valuable information and money by not implementing a two-factor authentication method.
2FA as a way to achieve GDPR compliance
Since the General Data Protection Regulation (GDPR) came into effect in May 2018, many organizations have had to pay significant fines:
- The French data protection office (CNIL) issued a €50M fine to Google for failing to obtain adequate consent from users when processing their data for personalized advertising.
- The UK Information Commissioners Office (ICO) obliged Marriott to pay a $121M fine for following the exposure of the personal information of approximately 339 million guests.
- British Airways paid a $22M fine after visitors to the airline’s website were diverted to a fraudulent site where the visitor would enter personal information.
- A German social network paid $24,500 because a breach exposed its users’ passwords, which were stored unencrypted.
That’s why some industries that work with time-sensitive and valuable information are adopting massively 2FA to add a layer of security. For example, OTP is a must-have in banking to protect bank users’ information.
Recommendations before enabling 2FA in any business
Businesses that want to start using 2FA software must ensure a successful implementation. To avoid risks, we share some best practices to help you implement 2FA and maintain it successfully in your business.
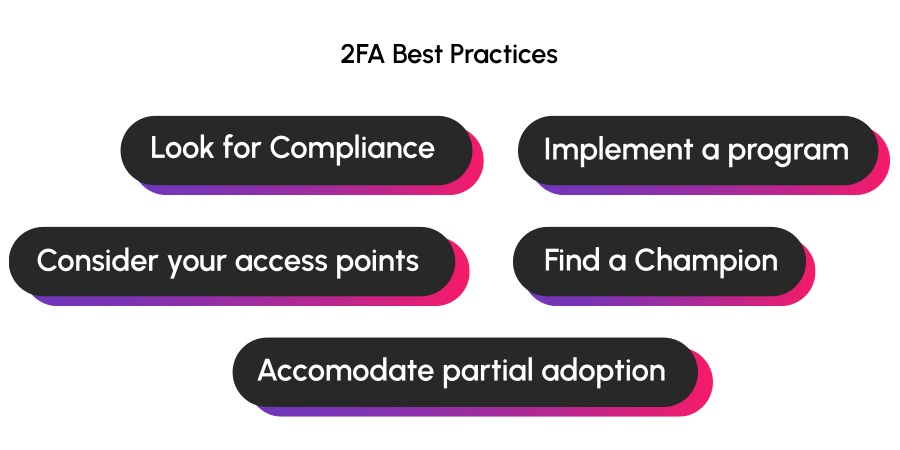
- Prioritize compliance: Certain standards ensure that a 2FA solution is more secure than others. We recommend choosing a two-factor verification solution that relies on standards-based cryptographic algorithms and authentication protocols.
- Keep your access points in mind: The hybrid work model is here to stay after the pandemic. That means your users and employees connect more devices from different locations. For an effective 2FA implementation, finding a provider that can accommodate all the locations where your users need to authenticate is critical.
- Find an internal leader: Your 2FA implementation will work best if you find someone on your team who can take charge throughout the process. Not only to encourage others to use the program but also to prevent errors and find improvements.
- Consider all factors: For various reasons, such as technology or cultural matters, you may be unable to have all your users switch to two-factor verification simultaneously. Find a solution that fits all your needs and allows you to incorporate users over time.
- Think of 2FA as a program: Implementing 2FA is not just about adding new software. To make it effective, create an implementation program with resources, training and employees involved.
In addition, try to answer these questions from users:
- Will this work on my phone/carrier? What if it’s not a company-supplied device?
- What if I forget my password or PIN?
- What happens if I lose my device, or it gets stolen?
- What if I change phones or SIM cards?
- How is my privacy protected?
- Does it work internationally? What if I’m offline?
- Will this work on my phone/carrier?
How you can implement 2FA
Thanks to technology, setting up two-factor authentication on your online accounts it’s easier than ever.
Soprano Authenticator enables financial services organizations, governments and corporations to take advantage of the penetration of mobile devices and dramatically improve the authentication of online access to services and corporate environments.
Authenticator manages the issuing and validating of one-time passwords and cryptographic checksums, communicating these to staff or customers using a secure mobile-device channel.
The system provides similar security to dedicated hand-held security tokens and soft tokens without the cost and management overheads that traditionally limit such devices’ applications in commercial environments.
You’re in control of the web application, ensuring control over which employees and customers have access to the two-factor solution. You can configure the system APIs to augment an existing two-factor solution or deploy Soprano Authenticator as a comprehensive, end-to-end robust and economical two-factor authentication solution.
2FA deployment methods:
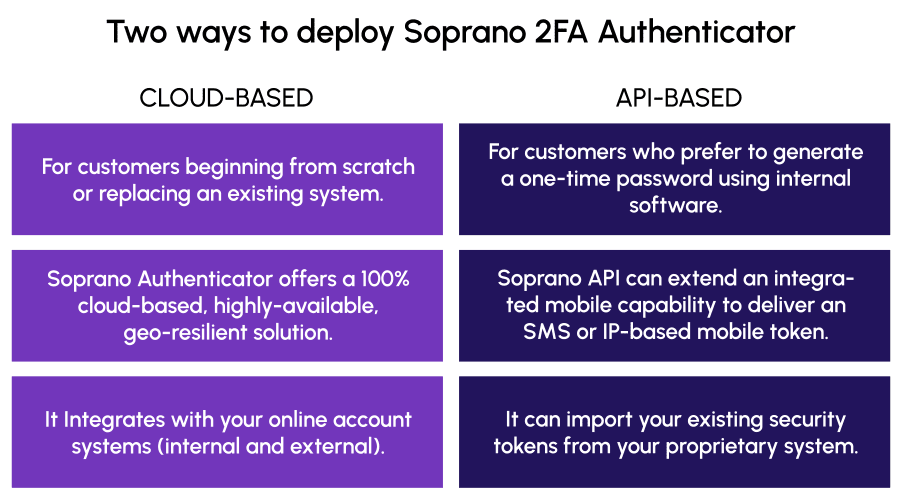
- 2FA API: For customers who prefer to generate a one-time password using internal software, Soprano Connect APIs can extend an integrated mobile capability to deliver an SMS or IP-based mobile token to global mobile users.
- 2FA CLOUD-BASED: For customers beginning from scratch or replacing an existing system, Soprano Authenticator offers a 100% cloud-based, highly available, geo-resilient solution.
Advantages of Soprano Authenticator
![]()
Enhanced Security
Soprano Authenticator cost-effectively enhances user authentication when many staff or customers access an online service.
Cost Savings
It’s possible to eliminate or reduce the labour-intensive manual processes currently used to compensate for the security exposures of existing practices.
Hardware tokens
Hardware tokens have a built-in expiry date, making it necessary to repurchase and redeploy after a finite period. Using a mobile phone solves this issue. With Authenticator, the existing problems of hardware tokens—life cycle, administration, logistics, registration, support and problem management— disappear, creating:
- Significant savings per token per year.
- Lower security appliance capital investment.
- Smaller ongoing internal and external operational expenditures for support.
Compatibility and Support
You can use the cloud-based Soprano Authenticator application to replace your current VPN infrastructure, or intelligent APIs can extend an SMS or IP messaging experience to your existing infrastructure.
Ease of Implementation
Soprano Authenticator integrates with your existing network access server or VPN aggregator. It uses industry standards and proprietary protocols, making integration into VPN solutions easy.
A whole web-based interface
The web-based interface (itself secured with Soprano Authenticator) allows your administration staff to register employees, customers, and suppliers as required, with simple integration from Active Directory for employee listings.
Extra layer of security
Soprano Authenticator sends cryptographically-generated passwords through a mobile data channel. This further negates any packet sniffing over the network.
Flexibility and Scalability
Soprano Authenticator has the flexibility and scalability to be deployed:
- As a single-site solution, allowing employees to be registered and managed efficiently.
- As a multi-site solution, allowing employees and staff to roam from site to site.
- As a web portal solution, allowing millions of customers to access your site securely.
- With two-factor verification as a transaction ID for specific business processes that require a particular audit trail.
- In “pass-through” mode for unregistered customers, allowing staged implementation and tolerance for partial customer adoption.
No Lost Tokens
Soprano Authenticator has no tokens to lose, replace, synchronise, or repair. Your customers, employees, or suppliers use their mobile phones to receive the token generated from your premises.
Reliability and Quality of Service
Soprano Authenticator is built with 24×7 high availability uptime, featuring load balancing and automated process monitoring.
Each process monitor includes alarms and logs to record failures. Soprano Authenticator is built with fault-tolerant fail-over to achieve carrier-grade robustness even at peak load levels.
Helpdesk and Operational Support.
Soprano Authenticator aids support personnel in help desk and administrative roles with fault logging, operations management and troubleshooting.
Reporting and Analysis
Soprano Authenticator features a report generation capability that allows support or systems analysts to view and print data such as login statistics and platform operations. This is beneficial for security audits and statistical purposes. Reports on usage and performance are available via the Soprano Authenticator portal.
Do you want to learn how our two-factor authentication solution can fit best in your business? Our team would love to talk with you.

