We’ve been hard at work here in Sydney to fulfill a number of customer requests with an updated version of our award-winning Soprano GAMMA app — including brand new features to help you improve productivity across your business.
What’s new in version 3.0? We’ve been working on the user experience and new features!
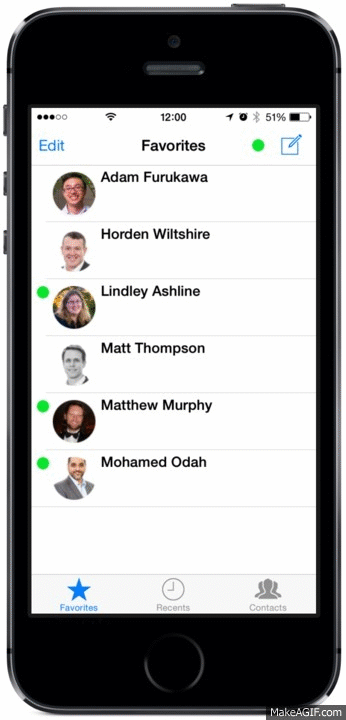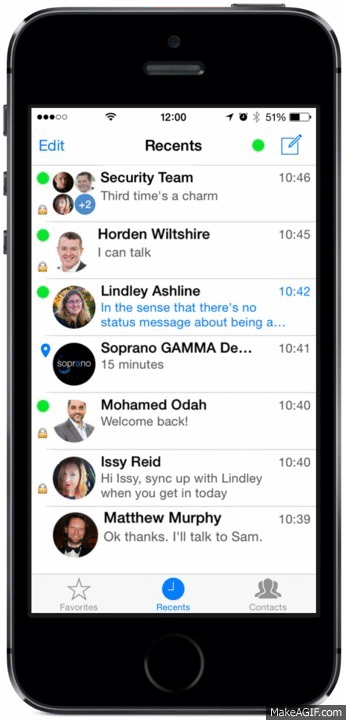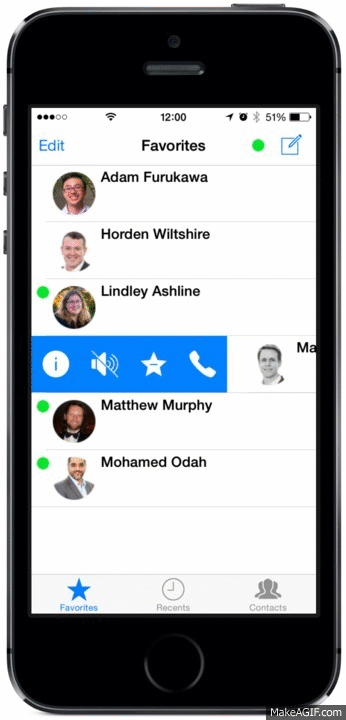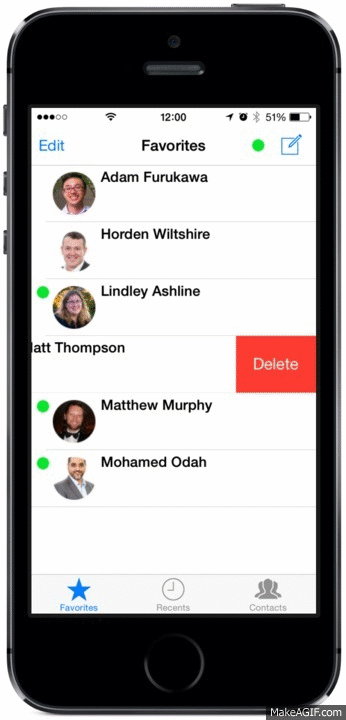
New Tabbed UI
We’ve created tabs in the mobile client to sort your Recent conversations from your Contacts and added a handy Favourites tab – making it easier to find that person you want to speak with!
Location, Location, Location
Corporate A2P accounts can now request location data from opted-in user devices for delivery receipts, read receipts, and messages.
